Dizit is rapidly expanding its team for the growing demand of Information Security Services organizations. Our focus is on three areas:
• Client Security
• Research & Development
• Information Security Education
Building up intellectual capital with customers across the country, Dizit is committed to providing an innovative set of services that address current security requirements. Dizit keeps focusing on Research & Development, Vulnerabilities Analysis and a few more services.
Security and Defense
The most extreme negative effect of technology advancement is an exponential increase in security breaches, for example, Cyber threats, Malware attacks, Phishing attacks, Web Application Attacks and so forth.
A lot of present security breaks likewise include inside workers like unapproved access to data, displeased employees and password misuse. All these security breaches may bring about extraordinary income loss, legitimate liabilities, lessened profitability and brand disintegration.
To avoid the above negative impact to an organization, Dizit provides the below effective information security services to customers:
Incident Response
Security Information and Event Management technology provides real-time analysis of security alerts generated by network hardware and applications. SIEM solutions come as software, appliances or managed services, and are also used to log security data and generate reports for compliance purposes. Security Information Event Management (SIEM) tools have capabilities of gathering, analyzing and presenting information from network and security devices; identity and access management applications; vulnerability management and policy compliance tools; operating system, database and application logs; and external threat data. A key focus is to monitor and help manage user and service privileges, directory services and other system configuration changes; as well as providing log auditing and review and incident response. SIEM can be deployed across the enterprise either in an owned model or as a hosted service. For customers who do not want to deploy data center infrastructure, related SIEM application infrastructure and trained manpower in-house can now use SIEM as a managed service from Dizit. We can manage Security Information and Event Management (SIEM) service collects, analyzes and stores logs from networks, hosts and critical applications. This service extends visibility beyond the network perimeter to the application layer to help businesses achieve more effective identification and mitigation of security threats, and compliance validation with numerous regulatory standards.
Patch Management
A fix to a program that eliminates a vulnerability exploited by malicious hackers. In computing, a patch is a small piece of software designed to update or fix problems with a computer program or its supporting data. This includes fixing bugs, replacing graphics and improving usability or performance. Though meant to fix problems, poorly designed patches can sometimes introduce new problems. Patch Assessment is the process of using a strategy and plan of what patches should be applied to which systems at a specified time. By the Patch Assessment Service, Dizit conducts an in-depth analysis of an organization’s existing patching practices. Our consultants review the patch management process followed. They consider aspects like documented procedures, the efficiency of the patch deployment methodology, i.e. automated or manual, patch testing and validation procedures, etc. Our consultants also review procedures for exceptional cases where patches are not deployable and the workarounds that have been implemented for the same. As a result of this service, the organization obtains a comprehensive understanding of the efficiency of the current patching processes, the lacunae in the existing procedures and the risks involved, which could adversely affect the continuity of their business. Detailed recommendations are provided, which enable an organization to bridge those gaps in their information security domain.
Firewall Auditing
A firewall is an integrated collection of security measures designed to prevent unauthorized electronic access to a networked computer system. It is also a device or set of devices configured to permit, deny, encrypt, decrypt, or proxy all computer traffic between different security domains.
Without proper configuration, a firewall can often become worthless. Standard security practices dictate a “default-deny” firewall ruleset, in which the only network connections which are allowed are the ones that have been explicitly allowed. Unfortunately, such a configuration requires a detailed understanding of the network applications and endpoints required for the organization’s day-to-day operation. Many businesses lack such understanding, and therefore implement a “default-allow” ruleset, in which all traffic is allowed unless it has been specifically blocked. This configuration makes inadvertent network connections and system compromise much more likely.
Many organizations implement firewalls without understanding the underlying technology or realizing the need for architecting a comprehensive policy for such firewalls. This leads to a false sense of complacency and security. Firewalls are used to prevent unauthorized persons from accessing private networks connected to the Internet. Only required data entering or leaving the Intranet passes through the firewall.
Through the Firewall Auditing Service, Dizit carries out a detailed review of the firewall configuration, either on-site or remotely, for secure practices, optimal organization of rules, etc.
Our consultants analyze and rectify configurations, simplify the organization’s rule-sets and related objects, and fine-tune the performance of the firewall and set appropriate operating system parameters. They also review random samples of log files for suspicious activity. As a result of a firewall audit, an organization obtains a firewall that is optimized for security and performance.
A detailed firewall audit provides a certain level of comfort that all possible security and continuity risks are being adequately addressed and also ensures that an adequate level of network integrity and security is achieved and maintained. Areas that are covered under a firewall audit are:
• Firewall Management and Administration
• Firewall Policies and Procedures
• Firewall Configuration
• Firewall Logical Access
• Operating System Logs
• Firewall Test
• Physical Security
• Continuity of Operations
A firewall audit service can simplify the management of your back-end Web applications. You can use it to virtualize the endpoint address, handle rate limit requests, and enforce access control. You can configure these items using the firewall audit service without writing any custom code.
Web Portal Security Services
A Web Portal presents information from diverse sources in a unified way. Apart from the search engine standard, web portals offer other services such as e-mail, news, stock prices, infotainment, and other features. Portals provide a way for enterprises to provide a consistent look and feel with access control and procedures for multiple applications.
There is increasing use of the internet by organizations to take advantage of its global reach. However, this introduces the requirement for pristine security controls related to processes and technologies that need to be deployed and securely managed. Our consultants conduct comprehensive security testing of the applications deployed for the Web Portal. All the server-side components of an application are examined. They include, but are not limited to, the following items that support the application:
• Application code
• Web servers and Database servers
• Directory and authentication devices
• Firewalls
• Network and enclave configuration required to support the application
• Operating system platforms for any of the above
Web Portal Security Service provides a comprehensive framework for assessing the security of the application processes and for reviewing the controls to examine their consistency with the business objectives. To accommodate a wide variety of security requirements, Dizit Portal integrates with other security infrastructure components to provide authentication, authorization, and single sign-on (SSO) capabilities. Dizit provides resources for portal administrators, IT Security professionals, and portal developers who need to configure, administer, or use portal security features.
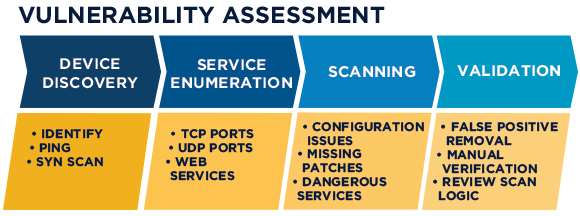
Vulnerability Assessment
A vulnerability assessment is a process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Examples of systems for which vulnerability assessments are performed include, but are not limited to, nuclear power plants, information technology systems, energy supply systems, water supply systems, transportation systems, and communication systems. Vulnerability assessments can be conducted for small businesses to large regional infrastructures.
Vulnerability assessment has many things in common with risk assessment. Assessments are typically performed according to the following steps:
• Cataloging assets and capabilities (resources) in a system
• Assigning quantifiable value (or at least rank order) and importance to those resources
• Identifying the vulnerabilities or potential threats to each resource
• Mitigating or eliminating the most serious vulnerabilities for the most valuable resources
Security measures should be properly targeted, and directly related to potential impacts, threats, and existing vulnerabilities. Failure to achieve this could result in inadequate security measures and excessive or unnecessary expenditure. An appropriate threat and risk assessment promotes better targeting of security measures and facilitates better decision-making. Through the Vulnerability Assessment and Penetration Testing Services, Dizit conducts a threat and vulnerability assessment of the network infrastructure devices. Our consultants review logs, services, application processes, trust relationships, access controls, and encryption. Our consultants also conduct an in-depth assessment of servers, routers, and security devices to determine the level of threat from external attackers using vulnerability assessment tools and manual exploration. Ethically and professionally conducted security and penetration tests help organizations to understand and assess the security vulnerabilities within their systems, as well as the associated threats and risks.
Penetration Testing
Dizit’s Penetration Testing company helps enterprise businesses quickly assess the security posture of their networks by safely identifying network and Application-level vulnerabilities before they are exploited by attackers. Dizit's security consultants use real-world scenarios to demonstrate the exploitation and how attackers can crack in to gain access to confidential data, networks, systems etc., that impact the business functioning of the organization.



